Christmas is not the time to get fired. If you get an email for your job termination, be careful it can be the new Dridex phishing campaign. Made appearance for the first time around 2011-2012, Dridex is a Trojan capable of using web injecting and receiving dynamic configuration files to steal money.
Earlier known as Cridex, this malware was based on the Zeus Trojan horse malware. Since then, it has been evolving, and recently it has been found taking advantage of the log4j vulnerability.
This post explains Dridex and how you can stay safe from it.
Discovered by security researcher and Twitter user @ffforward, it creates havoc and makes users fall for it.
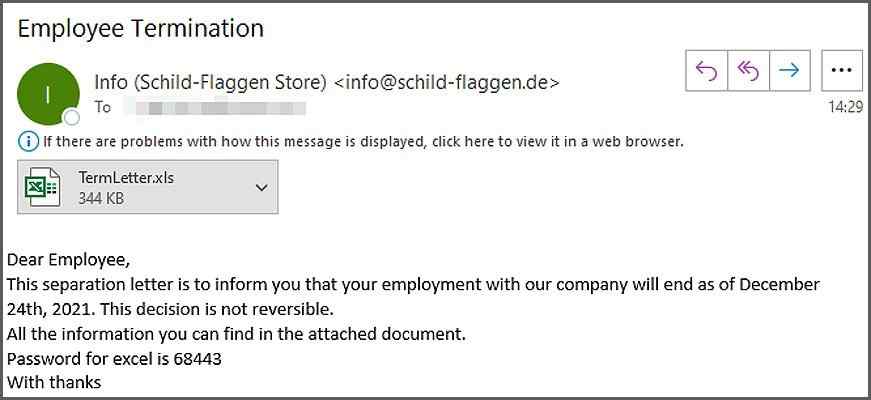
The hacker sends an employment cancellation email to fool users, which starts spreading the malware when the user opens and downloads the attachment. The folder is hidden inside under the ProgramData folder, and it spreads the malware from there.
What is Dridex malware?
Classified as a Trojan, Dridex is the most dreaded malware of the year 2021. Intended to target the victim’s banking information, Dridex steals sensitive information – banking credentials & financial access from within the victim’s bank account. Over the past 10 years, the Trojan has been updated to target more Windows users. To get the malware installed, hackers send spam emails, Hackers send spam emails, tricking the user into opening email attachments that have Dridex malware hidden within Excel or Word files. Dridex has impacted 3%-4% of organizations globally.
How does Dridex work?
To spread the malware, cybercriminals send emails pretending to be official. These phishing emails have Word and Excel files as attachments. Once the file is opened, the macro embedded in these files is triggered, and Dridex download starts to download. After that, the malware begins to steal banking details, and fraudulent financial transactions occur.
To steal this information, the malware injects a keylogger that monitors and records every keyboard input, enabling the attacker to steal banking credentials, login, and password details. In addition to this, Dridex can allow injection attacks to help injection attacks allow injection attacks to allow downloading more malware to trigger remote commands or inject malware code into specific programs. All this collected information is then encrypted into a package and submitted via P2P networks in XML or binary, depending on the version.
What makes Dridex dangerous & can it be detected?
Since it is a Trojan horse, Dridex can easily bypass antivirus software detection. However, if you use an antivirus program like Systweak Antivirus that regularly updates database definitions, detecting Dridex & such constantly evolving threats becomes easy.
However, if the security tool you are using works on signature-based threat detection, detecting Dridex won’t be possible.
To learn more about Systweak Antivirus, read the review.
How to stay protected against Dridex
Fortunately, protecting against Dridex is easier than detecting it. To achieve that, you need to keep the following points in mind:
- When opening emails with attachments from unknown senders, be careful.
- Avoid opening suspicious emails or files received from anonymous addresses.
- Download files only from trusted sources.
- Always keep applications, operating systems, and browsers updated.
- Use malware detection software that doesn’t use signature-based threat detection.
- Train staff so that they can identify phishing and spam emails.
How to remove Dridex malware
You can manually remove Dridex; however, doing so isn’t recommended. Therefore, to stay safe from malware threats and detect malware using antivirus programs that can detect and remove the latest threats like Dridex is recommended. Software like Systweak Antivirus can be used to detect and remove Dridex. Once you run a scan using the security tool and the threat is detected, the software will give you an option to quarantine it. After that, you will be asked to restart the system to apply changes. After Dridex or any malware is detected, changing banking and other credentials to stay secure is recommended.
Wrap Up –
Dridex, the banking malware, is rapidly spreading via malicious emails. Therefore to stay secure from such attacks, it is necessary to know how hackers operate. In this post, we have tried to explain how Evil Corp, the hacking group, uses malware to steal financial credentials and how to stay protected.
So, if you receive an email before Christmas stating you are fired, be sure to reach out to the security personnel before opening the email. The best way to stay safe from such attacks is to avoid opening emails received from unknown senders and downloading and opening attachments.
We hope you liked the information we have shared. Do share your thoughts in the comments section below.


 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!