New year is the time for new beginnings and learning experiences! It seems with this thought hackers have decided to break new grounds with a nasty piece of undetectable malware.
Patrick Wardle an Apple centric security researcher has spotted a new threat targeting Mac OSX dubbed MaMi malware. This threat resembles to the popular DNS changer malware that infected millions of systems in 2012.
DNS changer performed the attack by changing DNS settings on compromised machines, allowing attacker to direct internet traffic through nasty server and catch confidential information.
“Since there are already several (IMHO unrelated) malware specimens that perform DNS hijackering (that are named ‘DNSChanger’, etc), I decided to call is OSX/MaMi due to a core class the malware named: ‘SBMaMiSettings’ ” wrote Wardle.
MaMi malware is designed to hijack DNS settings on Mac OS devices, steal personal and confidential user information without being detected. It is unsigned Mach-O-64 bit executable
 Top 3 Recent Mac Malware Threatening SecurityDId you know about these three Mac malware that are threatening your digital security? Read to know more about the...
Top 3 Recent Mac Malware Threatening SecurityDId you know about these three Mac malware that are threatening your digital security? Read to know more about the...How was the Malware Spotted?
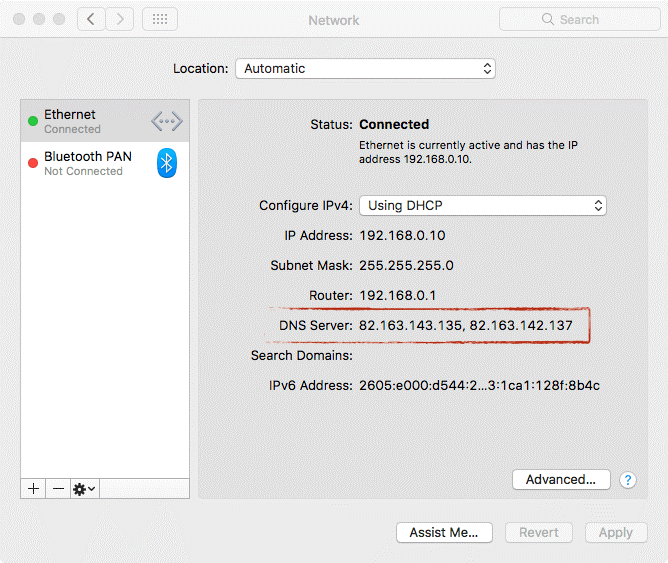
The sample of MaMi malware was obtained after a user reported about an infection on Malwarebytes forum. He mentioned that the Mac of his teacher was infected as DNS server was resetting automatically to 82.163.143.138 and 82.163.142.137.
Img src: securityaffairs.co
When the threat was discovered it was found that it goes undetected on all engines at VirusTotal meaning it is very advanced. But that is not the case as commented by the researcher, the threat has the capability of changing infected systems in offensive and determined ways.
How Does the Malicious Code Work?
The malicious code installs a new root certificate and hijacks the DNS server that helps attacker to perform number of nefarious activities like man in middle attack to steal personal information or inject ads.
Wardle,“By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle’ing traffic (perhaps to steal credentials, or inject ads).”
MaMi acts as a DNS hijacker and can perform following actions, but most of them are not available in current version 1.1.1:
- Taking screenshots
- Fakes mouse movements
- Downloads and uploads files
- Executes commands.
- Continues as a launch item
The nasty code was discovered on various sites but the source or distribution channel is still unknown. It seems that the developer is using age old method to spread infection i.e. emails, fake security alerts and pop ups on websites, or social engineering attacks.
Once the mac system is infected by MaMi it controls the security tool and uses it to install a new certificate (dcdata.bin) downloaded from the internet.
“By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle’ing traffic (perhaps to steal credentials, or inject ads).” explained Wardle.
How to Check if Your Mac OS is Infected?
To check if your machine is infected, go to terminal via System Preferences and check DNS severs code, if they are set to 82.163.148.135 and 82.163.142.137 then it is infected.
How to Stay Protected?
At present, none of the anti-virus software can detect malware, therefore you need to be extra cautious. To stay protected keep following points in mind:
- Can use a 3rd party tool such can firewall to detect and block outgoing traffic.
- Can use free open source firewall LULU, created by the researcher who detected the threat.
- Avoid enabling flash player requests.
- Don’t download third party product that mention they can secure your system from threats.
These simple ways will help you stay protected, also this threat is created specifically for Mac OS. So, for time being Windows users don’t have to worry. This is a serious attack as it is undetectable. Cyberwarfare is the emerging war front of 21st century therefore to stay protected against it we must gain knowledge. MAMI malware clearly shows how sophisticated the hackers are becoming. The OS that was fool proof from threats has now become the favorite target. This is just the glimpse of what hackers have for us this new year.


 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!