COVID-19, the pandemic, has changed the world’s equations. From making work from home, a new normal to a tenfold growth in the use of devices is witnessed. Due to this, the total internet traffic is anticipated to rise by about 50%, reaching 4.8 zettabytes in 2022. If digitization is going to grow at this rate, the world population will soon find itself on a new trajectory of cyber threats and attacks.
In 2021, we saw infrastructure breaches, SolarWinds hacks, Log4j, and other sophisticated attacks. Considering these ongoing attacks, as we head into 2022, it’s time to see what the future holds in terms of ransomware and cyber attacks. So let’s take a look at the ever-growing avenues of attack and what can be done to mitigate the risk.
Cyberattacks Aren’t Going Anywhere.
To enhance everyday life, the ever-evolving technology is bringing new and exciting advancements. Unluckily, for hackers, it is creating more grounds to steal data and digital identity. Some people to date think hackers only want to take advantage of individuals but their impact can reach far beyond that. Therefore, fighting these hackers who want to infiltrate your network is necessary. To get ready knowing about the threats is important.
Here we will discuss some of the popular threats.
Ransomware is a growing threat.
In the first quarter of 2021, ransomware attacks grew 3X compared to 2019. The number is expected to grow in 2022.
Ransomware’s name is self-explanatory. Unless money is paid; the virus that locks files will not go away, giving back the access. Usually, the ransom is asked to be paid in cryptocurrency. If the victim doesn’t pay, cybercriminals threaten to publish the data publicly, leaving the organization vulnerable.
Ransomware is one of the most dangerous threats that is also spread through physical access to the machine. To trick users into sharing details or clicking on malicious links hackers use Phishing emails and with the increase in digitization, these attacks are expected to target critical infrastructure, including water treatment facilities, gas pipelines, and hospitals.
The effective method of tackling these threats is by keeping employees educated testing employees to know if they are aware of the dangers. These practices, when implemented, reduce the chances to eight times.
The Internet of Vulnerable Things
Internet of Things (IoT) the number of connected devices is predicted to reach 18 billion by 2022. The biggest drawback of this massive increase in connected devices is giving more potential access points to cybercriminals to gain access to digital systems. For a long, IoT devices have been recognized as a specific threat as in the past, hackers have used connected household appliances to access computers or phones.
In 2022 we will undoubtedly see an increase in the number of attacks on IoT devices. Again, education and awareness will help protect against these vulnerabilities.
Steps we can all take to avoid becoming victims:
1. User Awareness
As cyber threats become more aggressive, significant steps to strengthen security need to be taken. Apart from implementing firewalls and sophisticated IT protocols, companies should educate their employees through training seminars; this will help prevent being a victim of data breaches.
People’s unawareness about the growing number of cyberattack methods helps cybercriminals design sophisticated attacks. Companies need to create policies focusing on employees handling sensitive information to prevent the onslaught of threats and attacks.
2. Cloud Security
With the help of the best cloud management software solutions, more and more businesses and organizations can keep their data encrypted and guarded. However, most services till data do not offer secure encryption, authentication, and audit logging. Therefore, a password manager and identity theft protection service is the best bet to stay protected by running an antivirus tool.
3. Use Antivirus
To secure the system from malware and other malicious threats, Systweak Antivirus is recommended.
Designed by Systweak, this excellent and robust security tool in real-time detects threats, blocks potentially malicious websites, and scans startup items for infections. All this helps stay protected against the latest and prevailing threats.
Also, you can set a schedule to run the scan when you want. You can perform Quick Scan, Deep Scan, and Custome Scan using the security tool.
To use Systweak Antivirus, follow these steps:
1. Download and install Systweak Antivirus.
2. Launch Systweak Antivirus.
3. From the left pane select the scan type – Quick Scan / Deep Scan / Custom Scan.
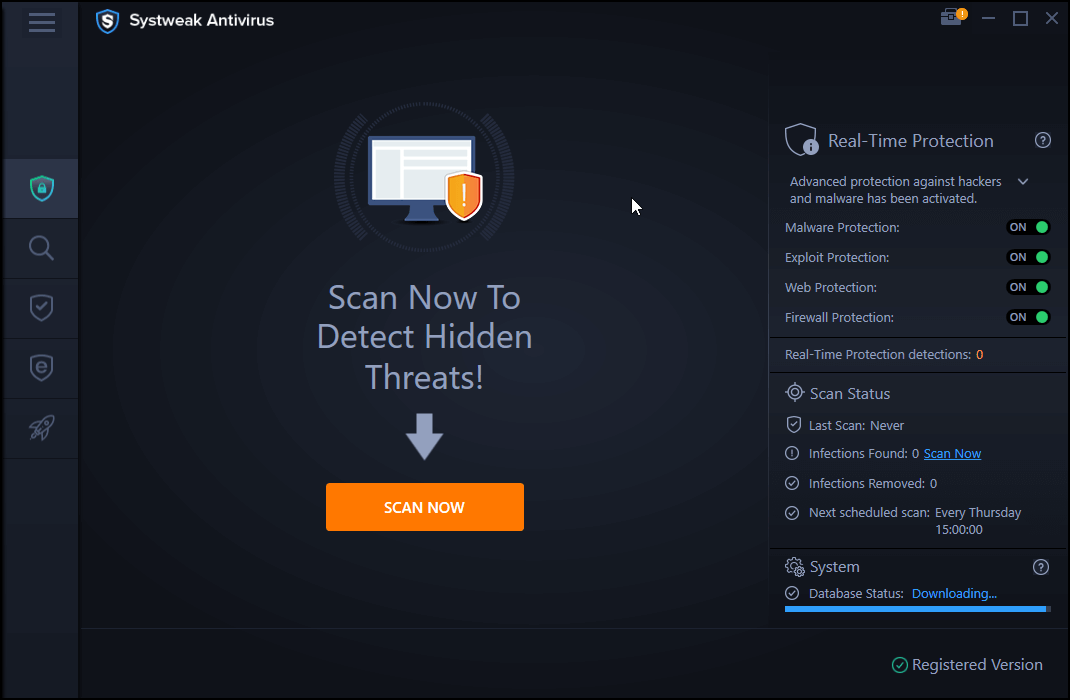
4. For thorough scanning go with Deep Scan.
5. Let the scanning process finish, this might take some time.
6. To clean detected threats click Protect Now.
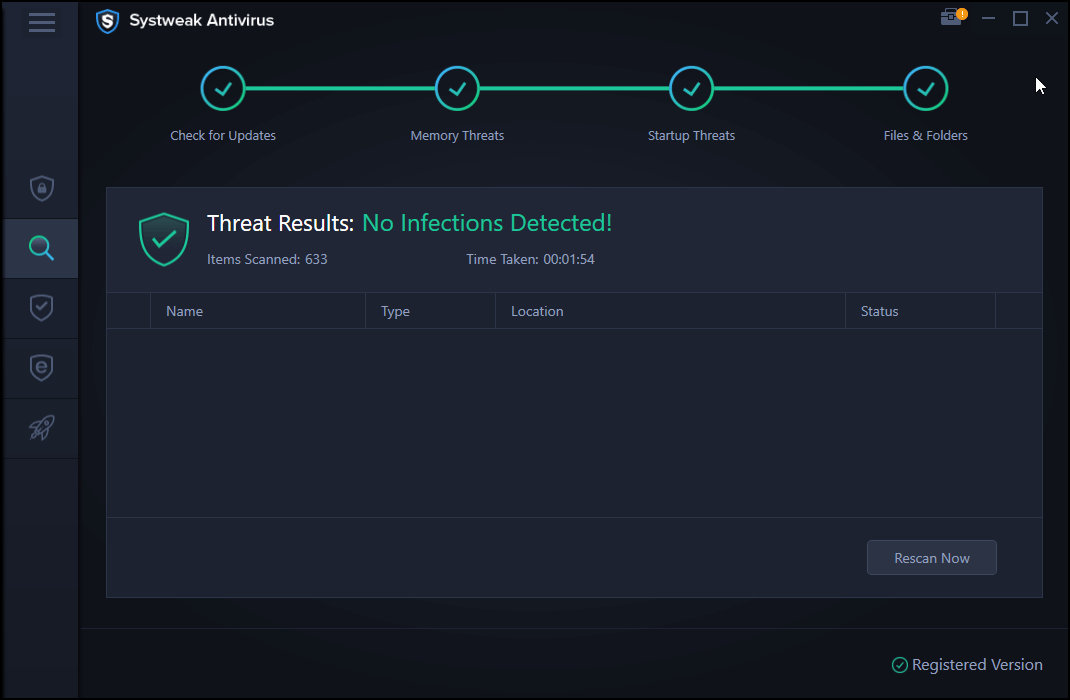
7. This is how you can keep your PC protected against malicious thretas.
Wrap Up
Neither cyberattacks will stop any time soon, nor is there a magic wand that can fill all the gaps in cybersecurity. To stay secure and protected concrete steps need to be taken. Without imparted awareness and education, organizations can’t stand against the attack.
Cybersecurity is not something that we can overlook for the growth of the business; we need to shift from cybersecurity to cyber resilience and implement trustworthy and sustainable measures. Everything will grow with time digitization, connected devices, and the supply chain. Therefore, to stay protected against cyber attacks, a trusted, secure, and protected digital environment needs to be built.



 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!