Believe it or not! Any Mac system connected to the internet is prone to be attacked by a cybercriminal via unauthorized websites, emails or someone who can directly access your Mac. But did you know, that there are built-in tools and utilities by Apple that can be used to efficiently maintain security and privacy on macOS?
Here are a few factors that need to be considered to secure your computer and keep your privacy from getting breached.
Standard Security & Privacy Practices Recommended for macOS.
There are no specific set of rules or practices that can make your macOS secure. If there would be any, hackers would have found a way penetrate them with an ease. It is the Unexpected and Diverse methods followed by macOS users across the globe that hamper the progress of these cybercriminals. From a wide variety of security practices followed, here are a few best ones that are included not because they are followed by many, but they actually make sense.

Points to be Kept in Mind Before Adopting the Best Security Practices:
Identification: The first step is to create a threat model which includes identifying your data that can be compromised and who can steal it.
Updates: Many of you might not know that Apple works round the clock, 24/7/365, identifying threats and creating security patches which is provided to all the users through updates. The least we can do to keep our computer safe is to keep it updated. Updates can be installed using the App Store application or can be downloaded directly from Apple’s support site.
Encryption. Encryption involves repacking your data into jumbled codes which when required can be unscrambled and accessed in an orderly way. It is a commonly followed practice to maintain full disk encryption which limits damage in case of an unauthorized data transfer. It is also advised to at least have an encrypted partition to store personal documents and credentials.
Backup. Any sort of system malfunction or compromise can easily be dealt with provided you have your data backup. Data can be backed up on an external storage device or can be uploaded to cloud storage services that can retrieve it anywhere. As a precautionary measure, it is important to encrypt the data locally before uploading it to the cloud. In this case, even in the 0.0001% chance that the data is compromised, it will prove useless as you alone possess the cryptographic key to that data.
Look before you click. As the famous saying goes by, it is important to predetermine what will the outcome of your next click. It is the responsibility of the users to judge the link before they click. Any wrong click would lead to a malicious page or install a fake application embedded with malicious malware and spyware.
Read more: Best Mac cleaning software to remove junk files
macOS Security: Installation
The first step for keeping your macOS PC secure is to install the operating system itself from a reliable source. If you install any unofficial or custom-built operating system, then the chances of your PC getting compromised are high and there isn’t the slightest chance of rectification as the malware files could be embedded into the operating system itself which was installed from a third-party source. The few authentic ways to Install macOS are:
- Boot into Recovery Mode by holding the Command and R keys at boot. Download the system image directly from the Apple website. This is the most commonly followed method which guaranteed an uncompromised installation of macOS. However, there is a limitation to this method which includes exposing the serial number of the PC with other identifying information over the network in plaintext.
- Another method that does not comprise the above limitation is to download the macOS from the Apple App Store and create an installable system image on a different partition of your hard drive.
- Apple also offers its users the facility to create a bootable USB Flash Disk which can be used to install the macOS on the computer. This installer can be made with an inhouse utility provided by Apple, known as ‘Createinstallmedia’.
macOS Security: Disk Encryption
A unique and very useful feature indeed of the macOS is the FileVault which provided full disk encryption. It was developed by Apple to protect your data and prevent anyone from stealing or tampering the data stored on your Mac. It is recommended to turn on the FileVault from system preferences after installing the macOS rather than creating an encrypted partition before the installation. To turn on FileVault, follow the steps mentioned below:
Step 1. Click on the Apple Menu, locate System Preferences and then click Security & Privacy.
Step 2. A new box will open. Click on the FileVault tab.
Step 3. Click on the lock sign at the bottom-left of the box and enter your admin credentials.
Step 4. Finally, click on ‘Turn on FileVault’.

macOS Security: Firmware Password
Now that the disk is encrypted, let’s work on the doorway to your computer. A firmware password prevents your Mac PC from booting up unless a few certain conditions are met. It requires a password and cannot boot up from any other device other than the one listed in the Startup Disk Preferences. This feature restricts anyone to access your data even if your PC is stolen as the Firmware Password can only be reset through the Apple Store which requires an original receipt as Proof of Purchase. The steps to enable a Firmware Password are:
Step 1. Startup your Mac by pressing the Command and R keys so that it boots to Recovery Mode.
Step 2. From the Recovery Window, choose Firmware Password Utility, from the utilities.
Step 3. In the new window, click on Turn on Firmware password.

Step 4. Enter a password of your choice twice and click on Set Password.
Step 5. Select Quit Firmware Utility and restart. You will be asked to enter a password every time your Mac PC restarts.

macOS Security: Firewall
One great feature that makes macOS different from other operating systems is the presence of several types of Firewalls. A Firewall is a feature that functions on the instructions provided to it by the user.
Application Layer Firewall: It is the default built-in Firewall which has the ability to monitor and block incoming connections. It does not check any outgoing connections. To check your firewall status, you can carry out the following steps:
Step 1. Open System Preferences and locate Security and Privacy.

Step 2. Click on the lock button on the bottom-left of this window and enter your admin credentials.
Step 3. Now click on the button next to Turn on your Firewall.
Step 4. Click on Firewall options and place a tick in the checkbox next to Enable Stealth Mode.

Third-party Firewall: Due to a few limitations of macOS’s default firewall, other software developers have developed certain firewall apps that can monitor both incoming and outgoing network connections. They are available on the Apple App Store and can be declared as trusted applications. Examples are Little Snitch, Radio Silence, Lulu, etc. are to name a few.
Kernel Level Packet Filtering: Packet Filtering in macOS is a powerful but complicated method to set up a firewall in the kernel of your PC. To activate this level of firewall, one must be familiar with pfctl configuration file. The user must manually add few codes into a file by the name of pf.rules or can also use the Icefloor application which has a graphical user interface. There are many books and websites that explain the subject of pf firewall and is used by large organizations which can block network access to an entire range of network addresses.
macOS Security: Disable Spotlight Suggestions
Did you know that any word you search for in your macOS using the Spotlight feature is sent to the Apple database along with your location? The same is true for Microsoft’s Bing search.
In order to maintain your security and privacy on macOS, it is recommended to disable Spotlight suggestions in the Spotlight app itself and in Safari’s search preferences. Remember that the Spotlight options are different and must be turned off individually. Also, if you have Bing Web Searches in your Spotlight options, then turn it off to prevent your search queries from being sent to Microsoft.
macOS Security: Password
Never keep your computer in an Open-to-all state. A password is necessary even though it is your personal computer and you are the only one with physical access to it. A password is the first level of security which can be quite a challenge to breach.
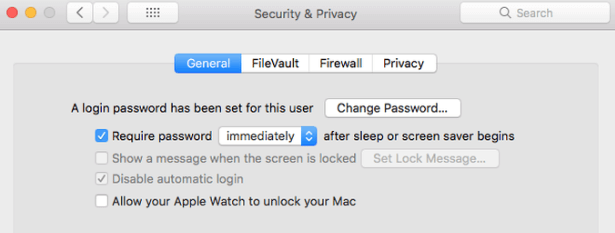
macOS Security: App Download Preferences
Your privacy and security matters on the type of apps you have installed in your system. Never download any installable files from third-party websites. Instead, download all that you need from the Apple App Store. There are two options available for macOS users: App Store and Identified Developers. I would recommend you enable the App Store button only. In older versions of macOS, there was a third option to Allow Apps from Anywhere which is strict NO and I would discourage you from enabling this option ever.

macOS Security: Domain Name System or DNS
Domain Name System is the standard used to convert the webpage address into a numeric internet address so that it becomes easy for computers to understand. For example, it is easy to remember website name in plain English – https://www.google.com/ but the same is converted to a set of numbers like – 172.217.9.228 which makes it easier for computers to understand. All the computers connected to internet consult DNS servers provided by your ISP.
I am sure you have understood by now that this process is not safe as the data is available for open access to all. For that same reason, it is recommended to use DNSCrypt that encrypts the data while sending and receiving from the DNS server. In this way, no one knows what request you have sent or what results have you received. Once enabled, you will not feel any difference in surfing the net, but you will be more secure than before.
DNSCrypt can be downloaded from the DNSCrypt official home page and requires setup once it is installed. To set it up, open System Preferences and locate the DNSCrypt icon at the bottom. Next, enable the options by clicking the checkboxes next to Enable DNSCrypt & Automatically Disable if Blocked.
macOS Security: Proxy
When we talk about Proxy, it means we are referring to a gateway between your PC and the internet. When you want to access a website, a request flow through the proxy server to the address you requested. Then result of the request flows back first to the Proxy Server and then to your PC. This is done because a proxy server can provide different levels of functionality like cache data, firewall, security and privacy as per user discretion. It requires complex programming to customize a proxy server according to your needs.
It is recommended to use Privoxy as a local proxy to filter web browsing traffic. It is a free application and supports both stand-alone and multi-user networks.
macOS Security: Browser
Although it is the most important program to surf the internet, it is also one of the major reasons for infections that occur in your PC. A browser is designed to download and execute any code from the internet. The browser developers have increased security measures to prevent malware and other malicious files from entering into your computer. But there is another problem that is developing. All browsers collect information about our browsing habits and use this information to show us data related to our search via Ads. This information along with our credentials and payment details can be misused by others. To maintain our privacy (which is our birthright), we can follow a few steps to minimize if not completely avoid privacy breaches.
- Never click on websites that when load, automatically download software on to your computer. If downloaded, then do not install it. Locate the.DMG executable file and trash it.
- All web browsers have extensions, add-ons, and plugins to make our task easier. These add-ons are developed because a required feature that must be present was not provided by the browser developer and was created by a third-party developer instead. However, many cybercriminals have found this as an alternative to hack computers and steal data.
- Many e-commerce websites store cookies on the user’s computer. These cookies are small files which store user’s pattern and movement on the web. For example, if you were interested in buying television and made quite a few searches for it, you would start seeing different TV’s in the list of recommended items on that website even though you were searching for something else. It is recommended to disable third-party cookies in the web browser settings.
Read More: Uninstaller for Mac to Remove Apps
macOS Security: VPN
Now that we have taken care of the browser, another factor that comes into our mind is the usage of a shared network. Anyone skilled enough could connect to the same public WIFI in a cafe or station and access your files and data. To avoid this, it is recommended to use a VPN Service.
A Virtual Private Network service assists the users to encrypt all the data and routes taken while sending and receiving requests. All the encryption and decryption processes do not affect user experience but keep the user safe and secure. Once you subscribe to a VPN service, it would provide an app that acts as a tool to configure the VPN services.
Not many know that macOS does provide a built-in tool that can be configured with your subscribed VPN settings. Open System Preferences and click on the network icon and locate a Plus button beneath the list of connections. A dialog box will appear where you need to select a VPN and fill in the Server and login details provided by the VPN Service.

macOS Security: Viruses and Malware
Despite all the precautions we take, there are still chances of virus and malware entering the system and creating havoc or capturing personal information.
With Apple claiming that there system is most secure, a common myth that macOS systems are immune to all types of malicious software emerged. But is it ture?
Truth be told, earlier there were more Windows Operating System computers in the world, hence cybercriminals developed bugs for it as it was profitable. But with the increase in number of Mac users, Cybercriminals have started shifting their unholy efforts, towards macOS users as well. And the truth is that no Operating system is immune to virus, malware, spyware, adware, ransomware, trojans, and any other such nasty threats.
Apple knew this fact all along and hence have inculcated Xprotect – an invisible anti-malware tool in macOS.
However, it seems that Xprotect is not up to the standard with the malware removal tools available in the market. Therefore, it is recommended that you invest in anti-malware that gives you most of it. One of the best software I have used over the years is Systweak Anti-Malware. As the name explains this powerful security tool for Mac helps detect and deleted spyware, virus, malware and other infections.
Download Systweak Anti-Malware Here
macOS Security: Backup
Backup is another word of making a copy of your files and saving it to a different location other than your system. Traditionally, backup was taken on external drives that could get stolen, corrupted and were expensive owing to their physical state. A new solution in the form of cloud storage services arrived which overcame the limitations of external devices. It only requires a speedy internet connection and user credentials. However, it is recommended to encrypt files and folders before taking a backup to avoid the mitigation of data theft.
macOS Security: Wi-Fi
One of the features which acts as a boon for many users is the fact that macOS remembers all the access points it has connected to. It is easy to identify network names among others and it also broadcasts all access point names each time it looks for a network. However, this boon can become a bane, as it comes under privacy risk. To remove all networks listed from the list go to System Preferences and locate Network and then go to the Advanced settings.
macOS Security: The Final Word
As I have stated already, anything that has a fixed set of rules is easier to break because cybercriminals know what to expect and will focus their energies to crack a specific code or hack a network. However, when a user takes so many precautionary measures, it becomes more difficult with every step taken. It is important to take charge of our security and privacy in our own hands and not rely on some software that is created on the basis of a sample of users who are facing the most common issues.
I have added all the points, I could think of and have applied in my Mac. If you know of any others or find issues with any of the above-mentioned steps, then do write in the comments section and I will surely find a solution to your issues.



 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!